In today’s digital era, using the internet has become an integral part of everyday life. From studying and working, to shopping and financial transactions, almost everything is now done online. However, as digital activities increase, cybercrimes like scams have also become more prevalent. So, what is a scam? A scam is an act of online fraud carried out with the intention of stealing the victim’s money, personal data, or belongings. Using a VPN is now also often recommended to enhance online security and reduce the risk of being scammed. Read on to learn more about scams and how to protect yourself from them.
Part 1: Discussing the Different Types of Scams
Scams can take several forms, such as phishing, tech support fraud, and crypto scams. Every year, millions of people fall victim to these various methods.

Phishing dan Vishing
Here’s an example of a scamming practice. Emails containing phishing links can trap victims; once clicked, the link may download malware onto the device or redirect to a fake website that appears legitimate. Usually, scammers pretend to be from a bank, a company, or a government agency to make the email look authentic.
In addition to email, scams are also often carried out over the phone (vishing), for example through VoIP services. In this scheme, the scammer claims to be from a trusted institution such as a bank or government agency. Sometimes, the victim will speak directly with the scammer, and other times they may only receive a voicemail from an unknown number. There are even automated systems (bots) that ask for personal data before connecting the victim to an "operator." Unwary victims may end up giving their sensitive information to cybercriminals.
Tech Support Scams
Tech support scams fall under the category of “vishing.” This scheme takes advantage of the victim’s trust in authorities—even large companies like Apple have been targeted by such tricks. Typically, scammers call pretending to be bank staff, company technicians, or representatives from official agencies. They try to scare victims by claiming their device is infected with a virus and needs remote access.
If the victim agrees, the scammer can install special applications, such as keyloggers, to record all activity on the computer, including passwords and important data. Sometimes, they’ll also claim there’s suspicious activity in the victim's account and ask for debit card details. Nowadays, scammers can even spoof phone numbers to make it look like the call is legitimately coming from the company. In reality, official companies never ask for sensitive information over the phone. So, always stay alert and never share important data through suspicious phone calls.
Crypto Scams
Crypto-related scams often occur through fake websites or apps and pump-and-dump schemes. For example, there are counterfeit crypto wallet apps that look convincing but are actually designed to steal your personal data or access your digital assets. Additionally, trading platforms with weak security are also vulnerable to hacking, putting users’ data at risk of being stolen. Pump-and-dump schemes happen when scammers deliberately drive up the price of a new coin or token. They create massive hype so that many people are lured into buying, thus raising the asset’s price. Once the price is high enough, the scammers sell off all their holdings at once, causing the price to crash and leaving new investors with huge losses. That’s why you should always be cautious and never get tempted easily before investing in the crypto world.
Part 2: How to Recognize If You Are Being Scammed
After understanding the meaning of a scam, here are some warning signs of fraud to watch out for. If you receive an email, SMS, phone call, or letter that is unexpected and unsolicited, it's best to pay attention to the following guidelines.

Asking for the user's personal information
Companies and government agencies are not legally allowed to ask for personal data from consumers. Information such as phone numbers, email addresses, bank account numbers, and passwords are considered sensitive data that must always be kept confidential.
Sender address that looks suspicious or unusual
If you receive an email claiming to be from PayPal but the name is written as "Paypal" or contains other spelling errors, it is almost certainly a scam. Checking the spelling of company names is simple, but it can be very helpful in preventing you from being tricked. Scammers often take advantage of your carelessness or worry to get the information they want.
Official representatives or company employees will not use strange or forceful methods when communicating. They will not make customers feel panicked, rushed, or pressured. Typically, you will also not be asked to reply to messages suddenly, especially without any prior notification or official contact.
Something that seems too good to be true
As the saying goes, if an offer seems too good to be true, it probably is. Be wary of scams that offer free prizes, huge discounts, or new products at no cost. Don’t easily trust unbelievable promotions, as they could be traps. Clicking carelessly on such ads can lead you to fake websites designed to steal your personal information.
Part 3: Simple Tips to Avoid Being Scammed
Limit the personal information you share online.
If possible, try not to share too much personal information on the internet. You can use a temporary (burner) email account to register or make transactions on less important websites. Think about it—how many free online services have you used and how many accounts have you created just for fun or for one-time use? Don’t forget that contact information like your name, phone number, and email address is actually easy to find online.
Because data leaks from hacked companies or websites happen frequently, you may not be as anonymous as you think. That’s why it’s so important to always limit the personal information you share online.
Use mobile banking apps.
If your card data is stolen and there are suspicious transactions, your mobile banking app will usually notify you right away. With a mobile banking app, you can easily monitor all spending and account activity. This is important because many scammers steal money gradually, bit by bit, so that victims don’t notice right away.
Use a VPN (Virtual Private Network).
With a VPN, your online activity becomes more private because it is not easily monitored by others, and your personal data is better protected from unwanted parties. When you browse using UC Browser, your internet data and conversations are secured with encryption features, making it harder to be intercepted or stolen by others. UC Browser also provides extra protection to help block viruses and prevent you from accessing dangerous websites. You can use UC Browser on various devices, and its security features are designed to keep you comfortable and safe from threats like malware or trackers. This way, you can browse the internet with greater peace of mind, without worrying about your data being leaked or misused.
Part 4: How to Use VPN Feature in UC Browser?
Step 1: Download and Install UC Browser
Download UC Browser from the official app store on your device to ensure safe access.
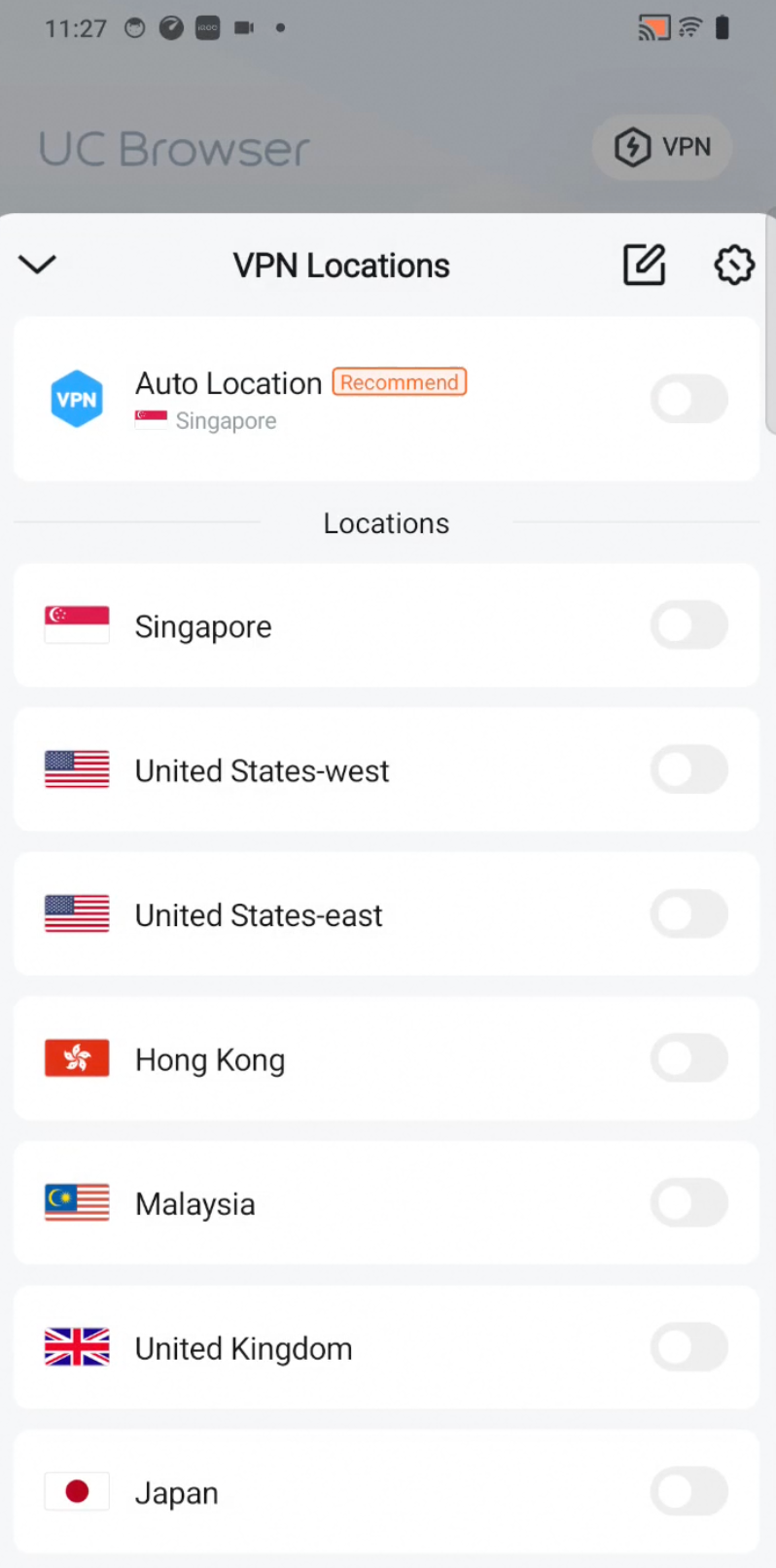
Step 2: Set Up VPN in UC Browser
Open UC Browser → Go to Settings → Enable the VPN feature → Select your preferred location/server
Step 3: Protect your privacy by using the VPN.
By using a VPN, your privacy while browsing the internet can be better protected. Your data and online activities will be encrypted, making them difficult for unauthorized parties to access. This is a simple yet effective way to keep your personal information secure.

Conclusion
In this digital era, privacy and security while online deserve special attention. Many of our daily activities have shifted to the virtual world, from shopping and working to communicating. The personal data we share can be misused if it falls into the wrong hands. This is where the importance of using a VPN comes in. With a VPN, your internet traffic is encrypted, making it much harder for unauthorized parties to spy on or steal your data. VPNs also help hide your location and online identity, giving you peace of mind when accessing the internet anywhere, including when using public Wi-Fi.
However, using a VPN is just one of many steps to maintain digital security. You still need to be alert to online scams, avoid clicking suspicious links, and never share personal data carelessly with untrusted parties. Combine a VPN with healthy digital habits to keep your privacy and security protected. Remember, security in the online world is our own responsibility, so always improve your knowledge and take extra precautions to protect your data and online activities.